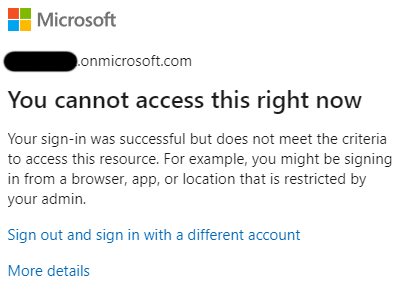
Conditional access policies for individual Power Apps will be general available in September 2022 (currently in public preview) and will give us a lot of control on how users can access Power Apps. With the use of Azure Active Directory Conditional Access, we can add extra layers of security to individual Power Apps to contain sensitive data. In my project we needed to create a conditional access policy to prevent a canvass app being opened on any mobile device. With Conditional access policies for individual Power Apps we were able to do this.
Setting up conditional access
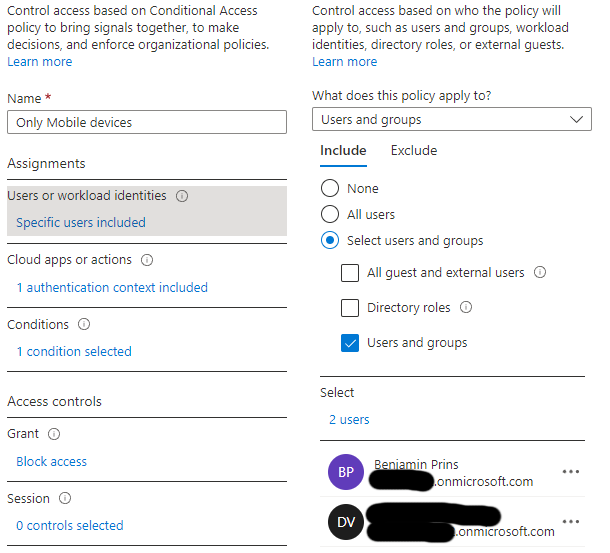
First we need to setup the conditional access policies in Azure Active Directory and connect it to an authentication context.
- Open the authentication context in Azure Active Directory.
- Click on New authentication context.
- Fill in the Name and Description.
- Select Publish to apps.
- Select an ID (it does not matter which one).
- Open the Policies in Azure Active Directory.
- Click on New policy.
- Give the policy a name.
- Select the users and/or group to apply the policy to
- Select the authentication context created earlier.
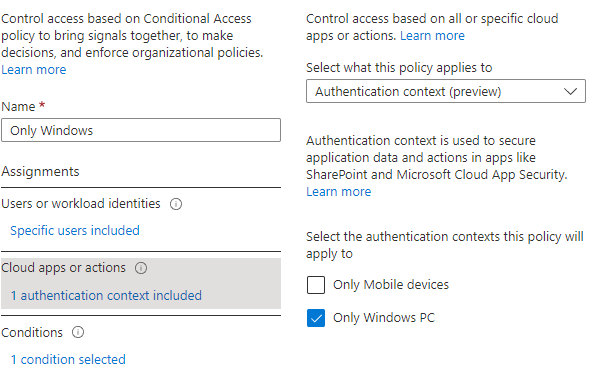
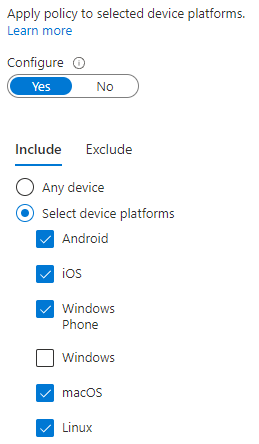
- Create the conditions and select all device platforms besides windows.
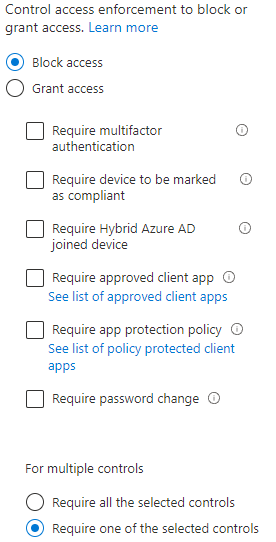
- Select the Block access under Grant to block all the device platforms besides windows.
- Click on Save.
- The policy is now created, but still needs to be connected to the canvas app.
Connect the conditional access to the canvass app
The policy needs to be connected to the canvas app with PowerShell.
- Open PowerShell as an administrator.
- Connect PowerShell to the Power Platform with the following command.
Add-PowerAppsAccount
- The PowerShell command requires the EnvironmentName (ID of the environment), AppName (ID of the canvass app) and the ID of the authentication context. The ID’s in my example are changed for security reasons.
Set-AdminPowerAppConditionalAccessAuthenticationContextIds -EnvironmentName Default-44444444-2222-3338-9b7f-0771d0c3301c -AppName b0111111-5555-4444-a22a-5af2574f1ed7 -AuthenticationContextIds c2
- The conditional access policy is now connected to the canvas app.